I hope that by now your site is running under HTTPS. If not, you may want to read Troy Hunt's [blog post(s)](https://www.troyhunt.com/ssl-is-not-about-encryption/" target="_blank ) on the subject. He does a great job explaining the WHY. If your site's running on Azure Web Apps under the default naming convention <yoursitename>.azurewebsites.net, you have the option to enforce HTTPS using the Azure certificate. However, this is not recommended. Most likely, you'll have your site running under a custom domain. If that's the case, you'll need a custom certificate. There are many ways to acquire a certificate for free but the easiest of all is to use [LetsEncrypt](https://letsencrypt.org/" target="_blank). There's even a handy[Azure Web App extension](https://github.com/sjkp/letsencrypt-siteextension/wiki/How-to-install" target="_blank) to help you set up LetsEncrypt on your Azure WebApps painlessly and for FREE!

Once you've [configured the custom domain name on your Azure Web App](https://docs.microsoft.com/en-us/Azure/app-service/app-service-web-tutorial-custom-domain" target="_blank) and [uploaded and applied the appropriate SSL certificate binding](https://docs.microsoft.com/en-us/Azure/app-service/app-service-web-tutorial-custom-ssl" target="_blank) to your site, you may want to enforce HTTPS-only traffic. Azure Web Apps, by default, allow sites to run under both HTTP and HTTPS. To enforce HTTPS-only traffic we need to hack the web.config with the following settings:
If you want to add [HSTS](https://www.troyhunt.com/understanding-http-strict-transport/" target="_blank) i.e. Strict Transport Security on top of this, you could change your web.config to look like this:
Also, if you're going down the HSTS route, you may also want to block iFrames and XSS attacks. The following custom headers in the web.config will allow you to do this:
P.S thanks to Azure CDA [Maxime Rouiller](https://twitter.com/MaximRouiller" target="_blank) for his input and his [blog post](https://blog.decayingcode.com/post/increasing-your-website-security-on-iis-with-http-headers/" target="_blank) on HSTS.
HTTPS Only - the new way
Azure WebApps now expose a new way to enforce HTTPS-only traffic. The new HTTPS Only setting means that you don't have to hack the web.config anymore since it's all managed at the AppService layer. To configure this you can use the Azure Portal:
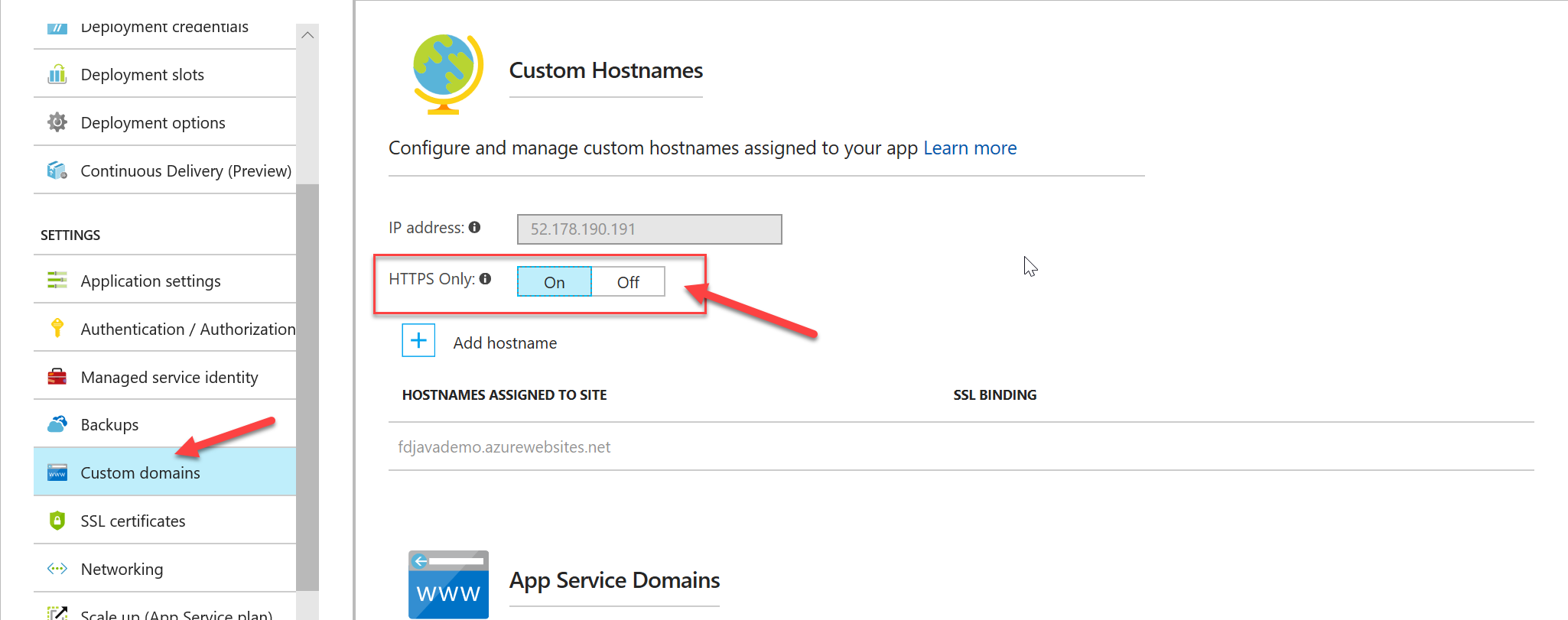
Alternatively, you can open the Azure CLI or Azure [Cloud Shell](https://docs.microsoft.com/en-us/azure/cloud-shell/overview" target="_blank) and run the following command:
az webapp update --resource-group <YourResourceGroupName> --name <YourWebAppName> --set httpsOnly=true
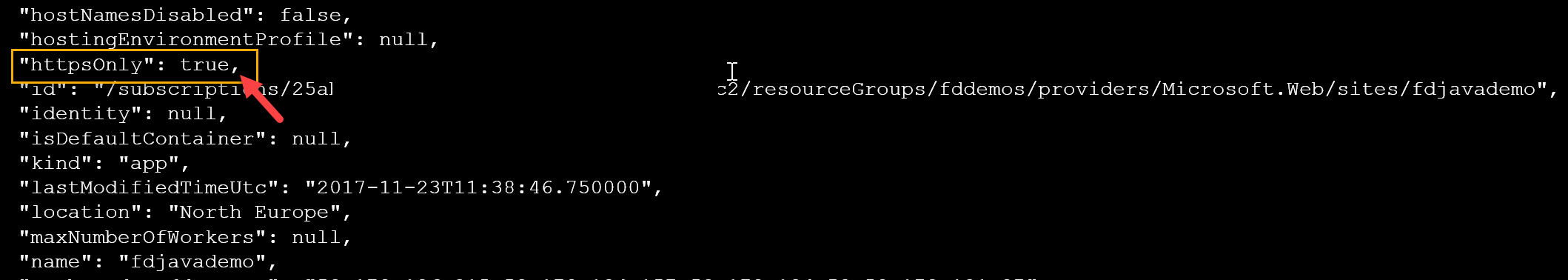
The output should contain the updated Application Settings including the HttpsOnly setting now set to true
Enforcing HTTPS only on Azure Functions
The awesome aftermath of this change is that we can use the same configuration for Azure Functions. Since Azure Functions run either on a standard or a special type (Consumption) of AppService plan, the HTTPS Only setting in also available. In the Azure Portal navigate to -> Your Function App -> Platform Features -> Custom Domain and set HTTPS Only to the desired value (On/Off).
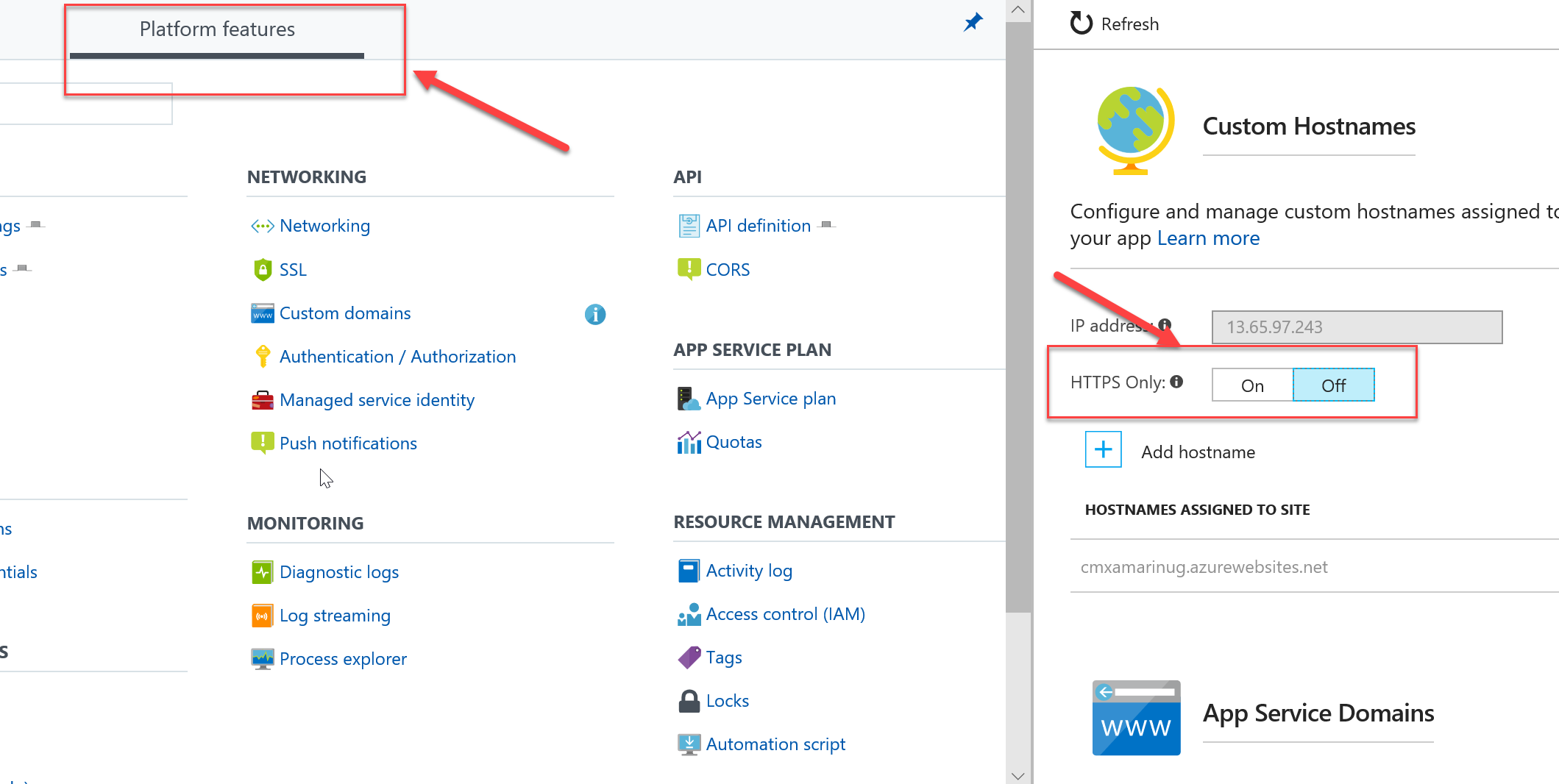
I know that this is a big thing because I've had people in the past reach out to me to ask how to implement this. For Azure Functions this this wasn't possible until now!
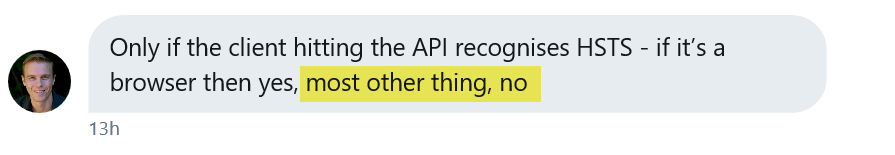
If you're thinking about HSTS, unless you have a public facing, browser-accessible API, then HSTS is not relevant in the Azure Functions context. To make sure I didn't get this wrong, I reached out to Troy Hunt (again) to ask his thoughts on this and I got this back:
Conclusion
With this new feature enabled on Azure AppService, it's extremely easy to setup HTTPS-only traffic and, consequently, improve the overall security of your site. No excuses now...