Ah [LogicApps](https://docs.microsoft.com/en-us/azure/app-service-logic/app-service-logic-what-are-logic-apps" target=_blank), the IFTT of Azure, the very young and lightweight "cousin" of Microsoft BizTalk. LogicApps is a great integration and workflow service that works great not only with Azure services but also with many SaaS products and 3rd party services. Think of LogicApps as a tool that you attach connectors to communicate with various components (sFTP, blob storage, email, Twitter etc) and grab data that you can manipulate or pass directly to another service. What I described here is IFTT but for enterprises with scalability, performance and flexibility in mind.
One of the cool things that you get with LogicApps is the ability to go totally off script and provide your own customised connectors. Alternatively you could use the generic HTTP Request trigger to create a sort of RESTful microservice. This is becoming a common pattern due to its versatility and lightness. The HTTP trigger is very popular and one that many LogicApp developers seem to favour. The HTTP Request trigger is a clever solution because it exposes a public HTTP endpoint. This, in extension, allows 2 things:
- You can nest LogicApps and have the parent(s) LogicApp call a child LogicApp
- You can call the LogicApp using a POST and even pass it a payload, if one's been defined and expected.
Unlike timers or triggers, HTTP Request connectors are invoked manually. The tricky part is finding and using the publically available HTTP URL. There are 2 ways to do this as I will explain in a bit.
LogicApp endpoint URL in the Azure Portal
This is pretty much self explanatory. Once you create your HTTP Request connector in the Designer in the Azure Portal and save the app, you will be presented with the URL as per the picture below:
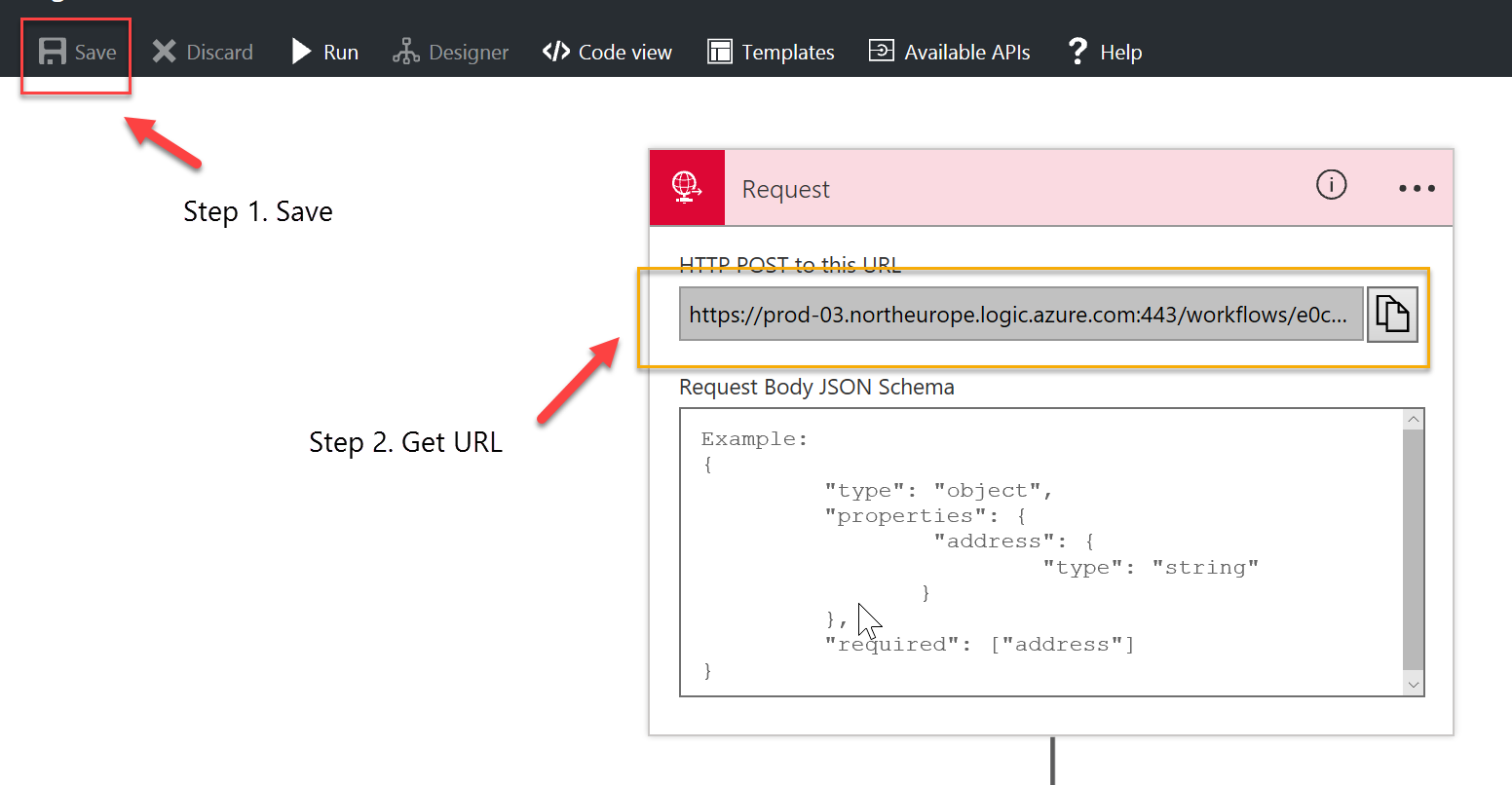
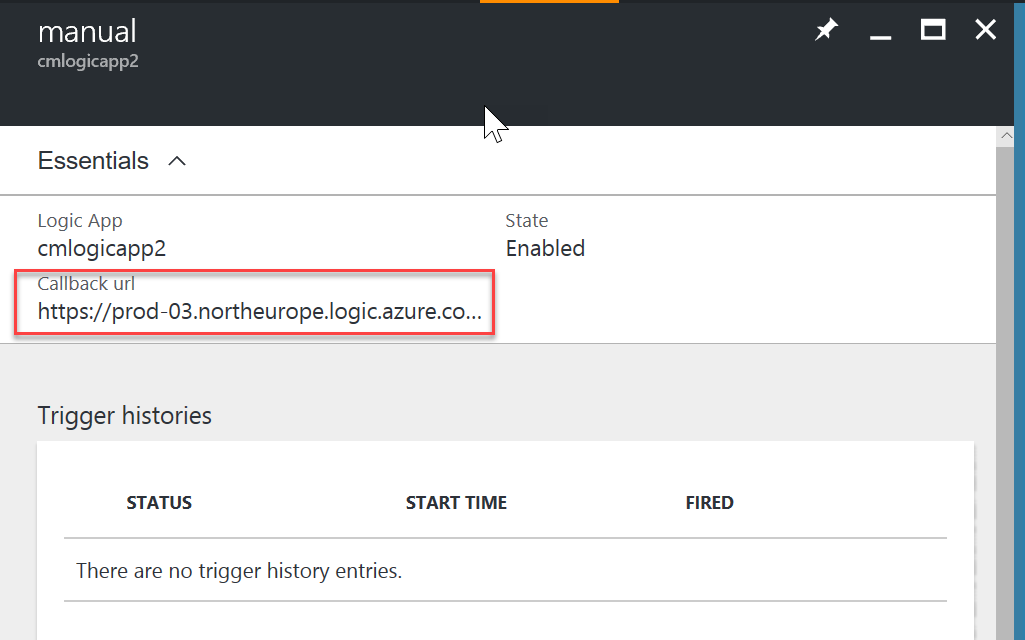
Another way to get the CallbackUrl through the portal is from the LogicApp Overview blade -> Click on Triggers -> select your trigger name -> and this should open a new blade that contains a reference to your CallbackUrl:
LogicApp endpoint URL using PowerShell
If you're like me, then you want to do everything programmatically. And Azure PowerShell (PoSH) is the best tool to do it. Unfortunately, the Azure CLI doesn't support LogicApps yet and as such we're "stuck" with PosH for now. I put "stuck" in quotes because I'm sure that by now you're aware that PoSH is cross platform and you can run it on Linux and MacOS. Right? Cool, I was just checking.
Ok then, let's get to work. The steps required (we'll take it from the top are):
- Log in to Azure
- Select the right subscription (if more than one)
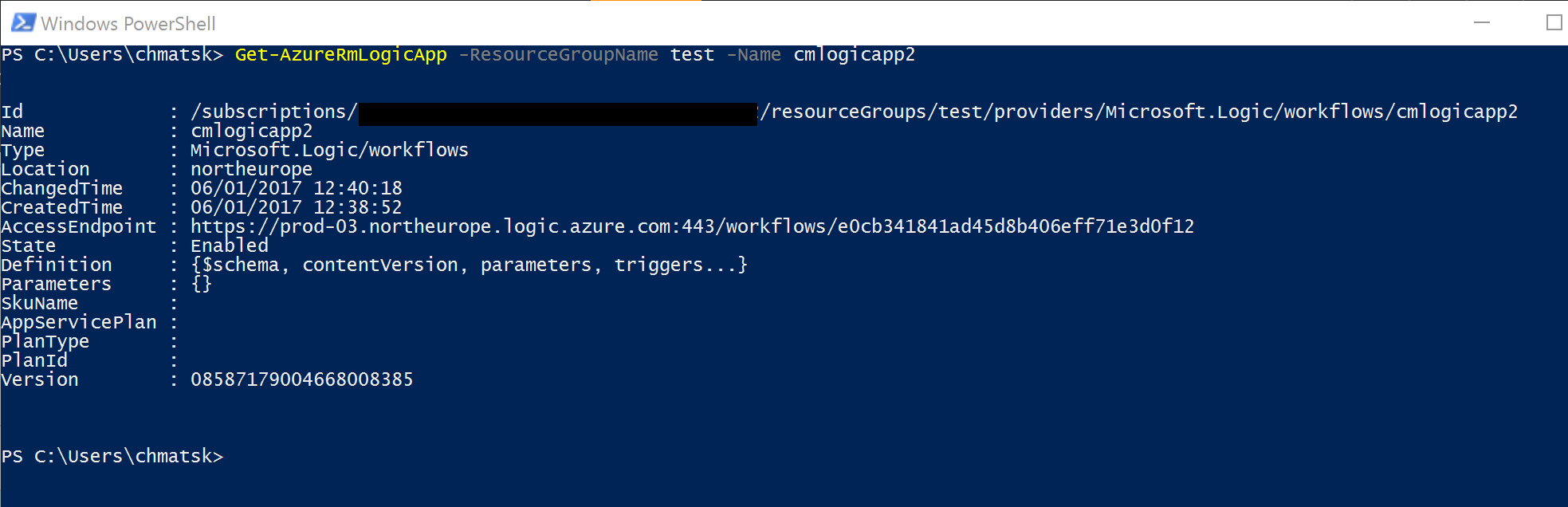
- Get the LogicApp (optional)
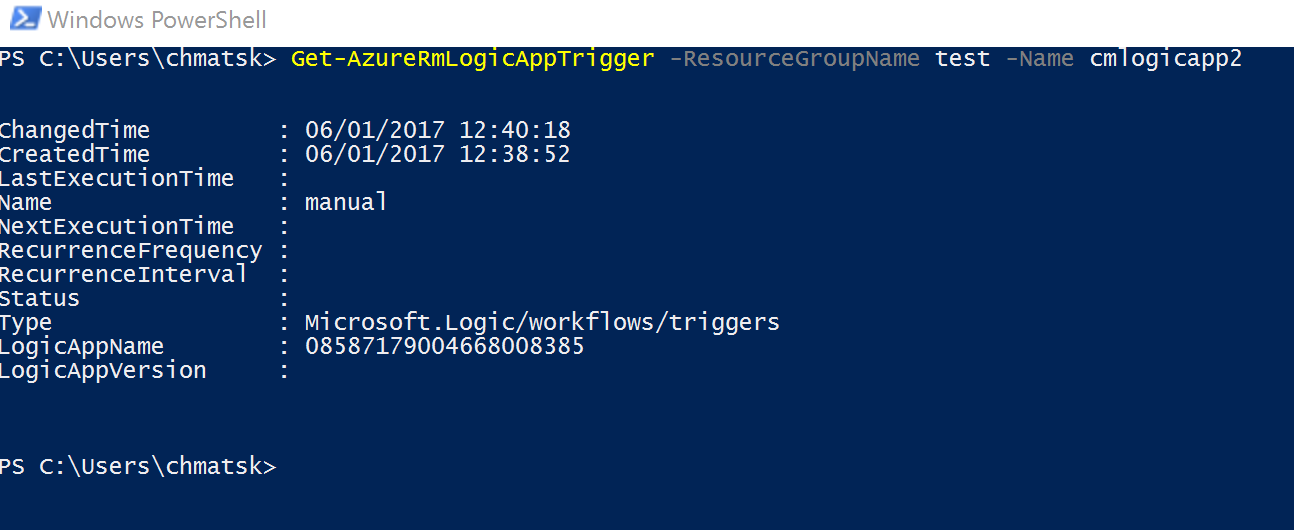
- Get the LogicApp Trigger (optional - unless you know the trigger name)
- Get the LogicApp Trigger URL
And now the PowerShell script to do all this:
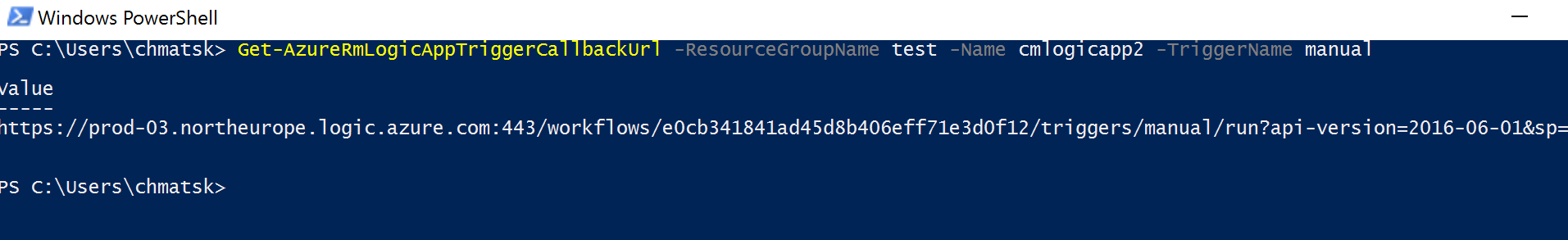
LogicApp public URL dissection and security
Access to the signature is secured using a Shared Access Signature (SAS) which is a SHA-256 hash generated using the Logic App secret key, URL path and parameters. Even though the Logic App has a section for Secret Keys, you only get the option to regenerate them. You never get access to the raw keys and all access to the endpoints is done through the use of SAS.
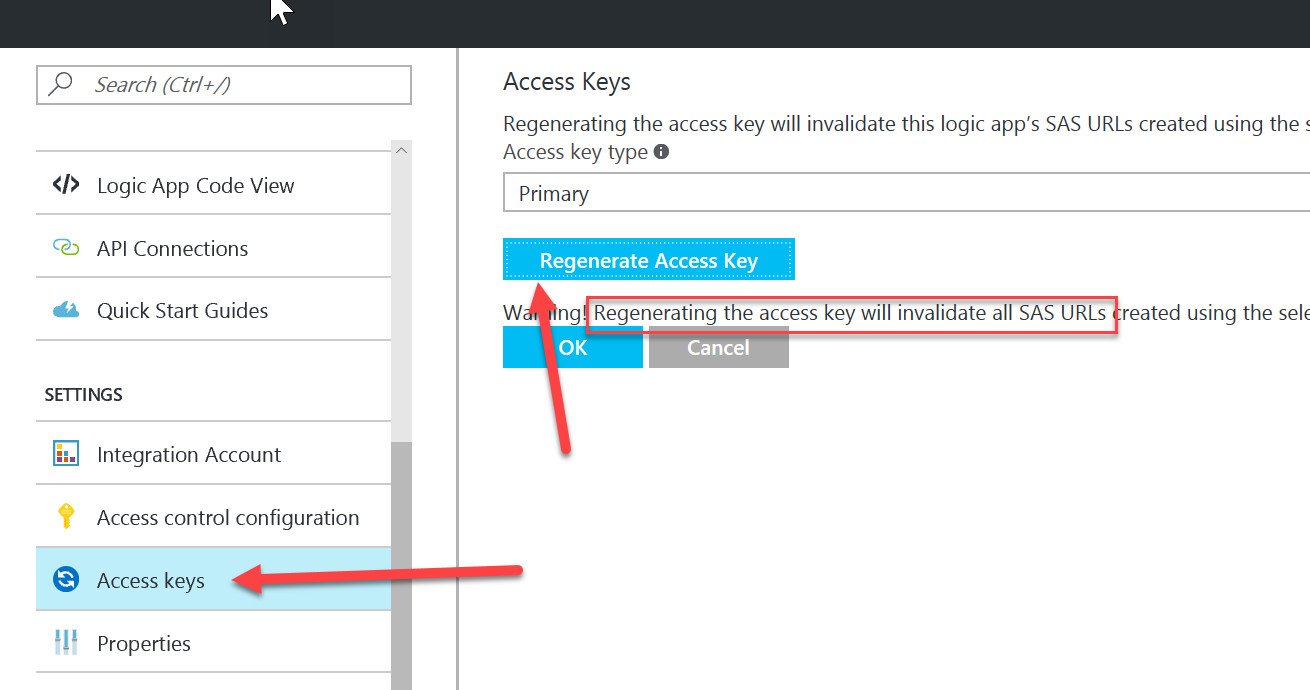
If you regenerate the LogicApp secret, the previous SAS become invalid and any code that uses it will fail.
Your logic app will only authorize calls to triggers that contain a valid signature created with the secret key. Hence the reason why this code is handy
So what does a LogicApp Callback URL look like?
https://prod-03.northeurope.logic.azure.com:443/workflows/e0cb341841ad45d8b406eff71e3d0f12/triggers/manual/run?api-version=2016-06-01&sp=%2Ftriggers%2Fmanual%2Frun&sv=1.0&sig=3B9tKN3epKBlRsHi3dNN64pRyeSDoO_IoBxLxYpnYpU
- Logic App URL trigger:
https://prod-03.northeurope.logic.azure.com:443/workflows/e0cb341841ad45d8b406eff71e3d0f12/triggers/manual/run - Logic App Api version:
api-version=2016-06-01 - Permissions:
sp=/triggers/manual/run(URL decoded) - SAS:
sig=3B9tKN3epKBlRsHi3dNN64pRyeSDoO_IoBxLxYpnYpU
Finally, there's a way to create time-limited SAS using the LogicApp REST Api. Using this functionality, you can share your LogicApp URL with 3rd party user outside your organisation using an SAS with an expiry date & time attached to it. This feature could prove handy if you want to showcase the functionality or show an early demo.
The URL should look like this:
https://management.core.windows.net/subscriptions/{subscriptionId}/resourceGroups/{resourceGroupName}/providers/Microsoft.Logic/workflows/{workflowName}/triggers/{triggerName}/listCallbackUrl?api-version=2016-06-01
The HTTP Request body should contain the following value:
{
"NotAfter" : "2017-01-10T18:25:43.511Z"
}
Note: your REST API call will need to contain an authorisation header which should be based on a Service Principal account credentials
Information about registering for and obtaining tokens can be found at the official REST Api [documentation](https://docs.microsoft.com/en-us/rest/api/index" target="_blank). As for the Service Principal (SP) requirement, jump to my [earlier blog post](GHOST_URL/service-principals-in-microsoft-azure/" target="_blank) for information on how to create a SP programmatically.